NAC
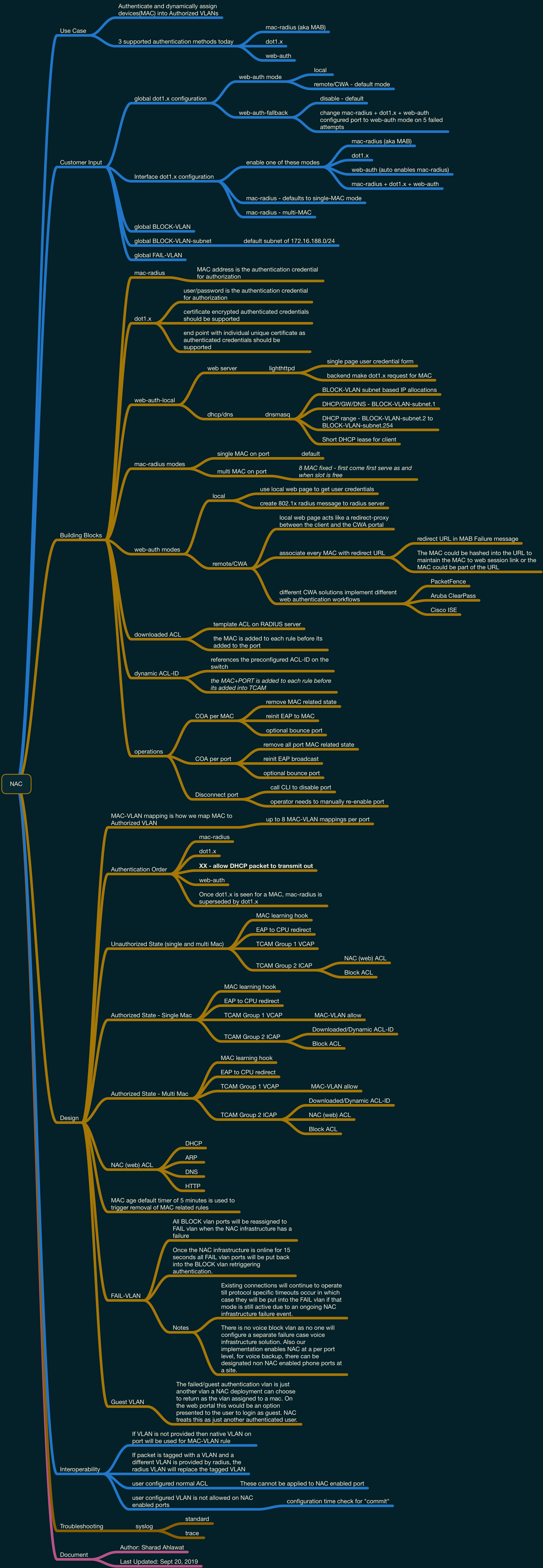

mac-radius (aka MAB)
dot1.x
web-auth
web-auth mode
local
remote/CWA - default mode
web-auth-fallback
disable - default
change mac-radius + dot1.x + web-auth configured port to web-auth mode on 5 failed attempts
enable one of these modes
mac-radius (aka MAB)
dot1.x
web-auth (auto enables mac-radius)
mac-radius + dot1.x + web-auth
mac-radius - defaults to single-MAC mode
mac-radius - multi-MAC
user/password is the authentication credential for authorization
certificate encrypted authenticated credentials should be supported
end point with individual unique certificate as authenticated credentials should be supported
web server
lighthttpd
single page user credential form
backend make dot1.x request for MAC
dhcp/dns
dnsmasq
BLOCK-VLAN subnet based IP allocations
DHCP/GW/DNS - BLOCK-VLAN-subnet.1
DHCP range - BLOCK-VLAN-subnet.2 to BLOCK-VLAN-subnet.254
Short DHCP lease for client
single MAC on port
multi MAC on port
local
use local web page to get user credentials
create 802.1x radius message to radius server
remote/CWA
local web page acts like a redirect-proxy between the client and the CWA portal
associate every MAC with redirect URL
redirect URL in MAB Failure message
The MAC could be hashed into the URL to maintain the MAC to web session link or the MAC could be part of the URL
different CWA solutions implement different web authentication workflows
PacketFence
Aruba ClearPass
Cisco ISE
template ACL on RADIUS server
the MAC is added to each rule before its added to the port
references the preconfigured ACL-ID on the switch
the MAC+PORT is added to each rule before its added into TCAM
COA per MAC
remove MAC related state
reinit EAP to MAC
optional bounce port
COA per port
remove all port MAC related state
reinit EAP broadcast
optional bounce port
Disconnect port
call CLI to disable port
operator needs to manually re-enable port
mac-radius
dot1.x
XX - allow DHCP packet to transmit out
web-auth
Once dot1.x is seen for a MAC, mac-radius is superseded by dot1.x
MAC learning hook
EAP to CPU redirect
TCAM Group 1 VCAP
TCAM Group 2 ICAP
NAC (web) ACL
Block ACL
MAC learning hook
EAP to CPU redirect
TCAM Group 1 VCAP
TCAM Group 2 ICAP
Downloaded/Dynamic ACL-ID
Block ACL
MAC learning hook
EAP to CPU redirect
TCAM Group 1 VCAP
TCAM Group 2 ICAP
Downloaded/Dynamic ACL-ID
NAC (web) ACL
Block ACL
DHCP
ARP
DNS
HTTP
All BLOCK vlan ports will be reassigned to FAIL vlan when the NAC infrastructure has a failure
Once the NAC infrastructure is online for 15 seconds all FAIL vlan ports will be put back into the BLOCK vlan retriggering authentication.
Notes
Existing connections will continue to operate till protocol specific timeouts occur in which case they will be put into the FAIL vlan if that mode is still active due to an ongoing NAC infrastructure failure event.
There is no voice block vlan as no one will configure a separate failure case voice infrastructure solution. Also our implementation enables NAC at a per port level, for voice backup, there can be designated non NAC enabled phone ports at a site.
standard
trace